Cyber Risk: A guide to protecting your business
Making sense of cyber risk
Business of all sizes, in every industry, increasingly rely on technology and data - but businesses often underestimate the risks posed by cyber threats.
Whilst cyber attacks can vary in terms of persistence, sophistication and impact, the financial and reputational risks are too important to be ignored.
This guide aims to demystify some of the key elements of cyber risk, so you can take the necessary steps to protect your business.
1) Assess: understand potential cyber exposures of your business
Information/data:
If your business holds any sensitive or personal data you face an increased cybersecurity risk.
Websites:
Cyber criminals are constantly targeting online vulnerabilities to spoof websites, steal data and disrupt on-line activity.
People:
Human error and insider threat can compromise your cyber security. High profile senior figures can also make businesses a more attractive target.
Intellectual property & trade secrets:
This can be one of your most vulnerable assets, putting you at high risk from hostile insiders and external attackers.
Internet of Things (IoT):
With varying security standards on these devices and 30 billion IoT connections expected by 2025, each connected device represents an attack surface and is an
avenue for compromise
Contracts:
Consider any contractual obligations for cyber security between your business, clients and third parties.
Information and operational technology:
Any business that uses technology or links operational technology to their networks has an increased cyber risk.
Key threats facing businesses:
Ransomware
Once a network is infected with ransomware, the malware denies you access to your systems and files, with a financial and/or destructive motive. More recently, ransomware gangs have shifted the approach to exfiltrate data from systems prior to the ransomware being executed, with a threat to then publish the data publicly to apply further pressure for ransom payment.
Social engineering
Covering a range of malicious activity, influencing users through psychological manipulation by creating a sense of urgency, curiosity or fear to perform actions or disclose confidential information, often through Phishing Emails. The data obtained is then used to gain access to systems or engineer the transfer of money.
Example: Humans want to trust and help one another. After doing research into a company, cybercriminals target an employee in the accounts department with an email that looks to come from the CFO for an urgent money transfer to ensure that a crucial time-critical deal can be completed.
As a result of applying pressure as ‘CFO’ and with the employee wanting to be helpful, the transfer is made quickly as directed.
Data breach
Confidential data is accessed and in some cases used to extort companies, or the data is just sold on the dark web. Data could include personal banking information, Personally Identifiable Information, Commercially sensitive data or Intellectual Property.
Example: Following a cyber attack, a professional services firm needs to notify all customers affected that their personal information may have been exposed. As well as the cost of sending out thousands of notifications, the company has to cope with the extra volumes of telephone calls, emails and potential third party claims for damages and loss of client trust.
Human factor
Whilst there is a malicious element in some cases, the majority of incidents are non-malicious and as a result of a lack of awareness, training or sometimes concentration. With many businesses changing to reflect a remote workforce requirement, this is also a risk that needs to be managed.
Examples of cybersecurity threats caused by human factors include:
- Poor password security
- Accidentally clicking on malicious links and attachments
- Not following processes and procedures, Misdelivery of sensitive information.
Third-party risk
This is the potential threat presented to a business and its operations from supply - chains and other third party outside vendors providing services and having access to your systems and data.
Example: The SolarWinds attack impacted globally even though they are a US tech firm. Malicious code was added to the company’s software system ‘Orion’ and pushed out via a software update to all of their clients who use their services to manage IT resources. This created a back door to their customers systems which exposed all of the organisations.
Notifications were made by UK clients.
2) Protect: determine your appetite, prioritise and take steps to manage your risks
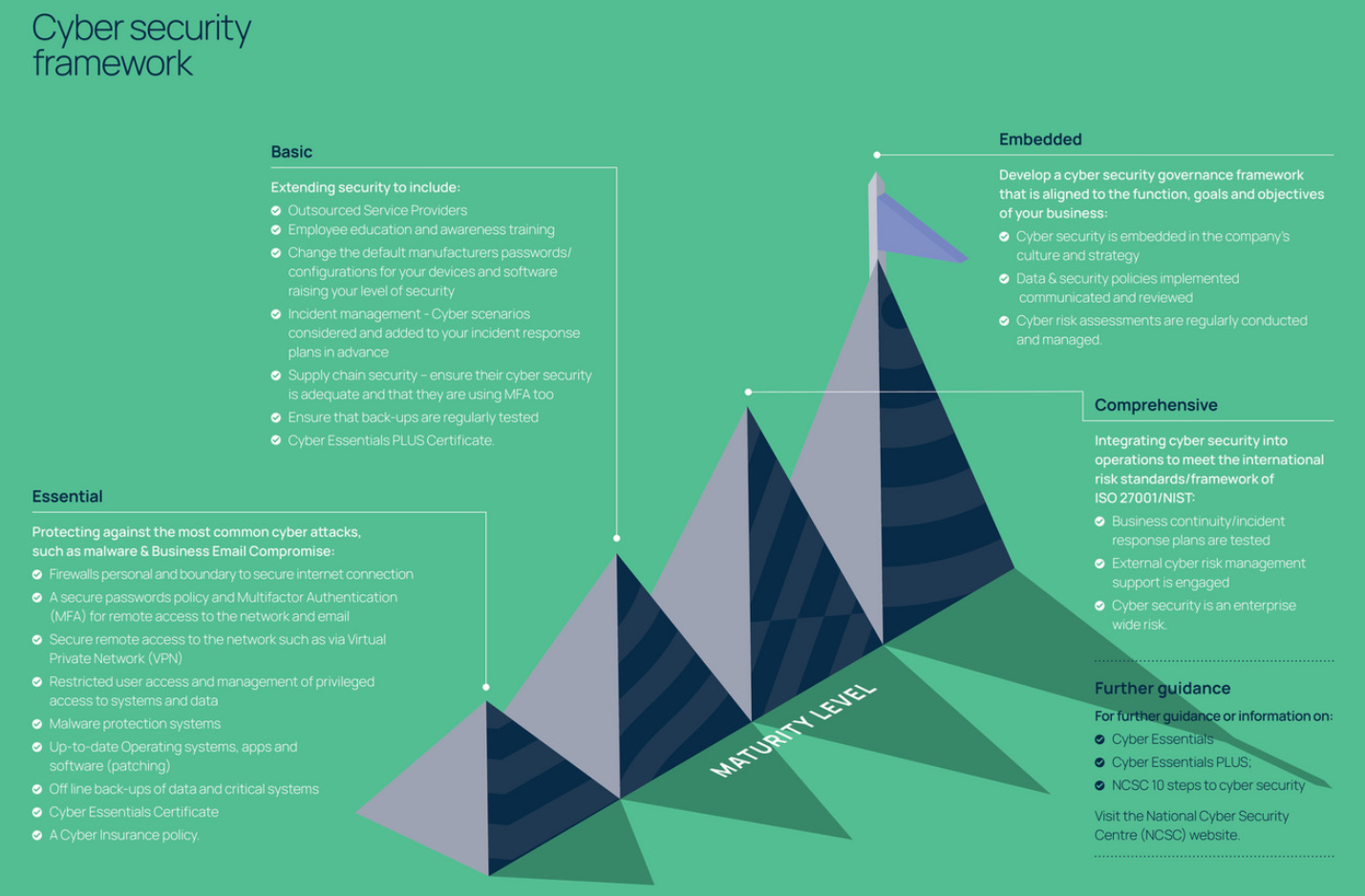
3) Respond & recover: practical advice for business resilience
Do
- Conduct regular security assessments and keep all IT software updated
- Implement MFAto remote network and email access
- Regularly review access and administration rights of employees
- Create a positive security culture. Educate employees about different cyber threats as they are one of the best lines of defence
- Have an incident response plan in place, with a copy kept offline in case you can’t access your systems. Have designated people responsible for implementing the plan in the event of an attack to ensure the business responds quickly
- Back up - Identify the data you need to back up and keep your back-up separate from your system. Ensure that back-ups are kept offline and not connected to the network, so not accessible by staff
- Ensure physical security is maintained at your premises, restricting access to data, portable equipment and server rooms etc.
Don't
- Be complacent about cyber security, keep it front of mind
- Solely rely on your IT team and antivirus programmes to protect you against cyber threats
- Negotiate with cyber criminals. Paying a ransom wont always end in regaining access, it can fund terrorism and may only fuel them to continue attacking companies – seek specialist help!
- Destroy any logs or computers after a cyber attack, they may be needed by experts for any investigations into the attack
- Forget to remove former employees access to any systems or data immediately to avoid malicious intent
- Forget to pass your cyber security requirements onto your critical service providers and third parties.

Cyber insurance as a risk management tool
A cyber incident can affect your ability to operate, impact your financials, and damage your long-term reputation. Whilst Cyber Insurance will not protect you from an attack, it allows for some of the financial risk to be transferred and assist with mitigating disruption.
Having the support of a specialist insurance broker will help identify the risks that are unique to your business. Our team of 25 UK based Cyber Insurance experts have an in depth understanding of policies that are best suited for all types of business and sectors. From corporate to SME businesses, we take an integrated, holistic approach when defining our clients’ business risks, providing the most effective Cyber Insurance solutions to help protect your company.
As a trusted adviser, we understand that good risk management goes beyond just securing a Cyber Insurance policy. We also help our clients to develop their risk management procedures by providing regular advice and recommendations. We make sure that you know how your insurance policy can respond to a cyber-incident, and have a strong, experienced claims handling team to support you during the claims process, should an incident occur.
Demystify: De-coding Cyber myths
The Association of British Insurers (ABI) has revealed that the claims acceptance rates for Cyber Insurance policies are one of the highest across all insurance products.
Confusion has arisen due to claims relating to cyber incidents being rejected, as they were brought against other classes of insurance policy such as Property or Kidnap & Ransom, which are not designed to cover the full range of cyber threats.
A recent Verizon report found 58% of cybercrime victims were categorised as small businesses. Smaller organisations often lack the resources necessary to invest in IT security or provide cyber training for their staff, making them an easier target.
Any business that relies on a computer system to operate has a risk. Two common sources of cyber claims are from criminals using fraudulent emails to request the transfer of funds, or ransomware attacks causing severe business interruption and potentially large financial losses.
Outsourcing to a third party doesn’t mean outsourcing your responsibilities for the protection of data as confirmed by GDPR. If your IT service provider is compromised it could significantly impact your business operations and financials too. Even if you claim against them for damages, it could take time and their liability to you could also be limited.
You can have the best defences in the world, but IT security can’t always protect you from all threats including the human factor or exposure via third party vendors or suppliers. They say you are only as strong as your weakest link. Whilst your IT director will be critical in the incident response, they will unlikely have the experience or specialist knowledge that might be required during a cyber attack, such as knowledge of hackers, variants of malware, how to negotiate ransoms or the dark web.
Some policies can include a very small amount of cyber coverage, but it is usually very limited in what it provides for.
In addition to this, The Prudential Regulatory Authority (in January 2019) and then Lloyd’s (in July 20 have made insurers put into action plans to reduce what has been identified as ‘silent’ cyber exposures - either by excluding or providing affirmative coverage.
Did you enjoy this guide? Download a copy here



